The digital landscape is rife with various forms of cyber threats, and phishing remains one of the most prevalent and damaging among them. Phishing attacks involve the deceptive practice of luring individuals into divulging sensitive information, such as personal credentials or financial details, by impersonating trustworthy entities. Over the years, cybercriminals have continuously evolved their techniques to make their fraudulent campaigns more convincing and harder to detect. One such technique that has gained prominence is the abuse of open redirects.
An Open Redirect vulnerability (CWE-601) is present when a web application accepts, without validation, user-controlled information that redirects to an external website. Let’s take a look at the following example:
https://legitwebsite.tld/login.html?redirect_to=https://legitwebsite.tld/page2Within the URL provided above, an application logic is at play. This logic entails that following the execution of a particular operation, the end user is ultimately directed towards the URL specified within the “redirect_to” parameter. However, a vulnerability emerges in instances where the application neglects the validation of the URL supplied as input. This disregard for validation opens the door for a malicious adversary to manipulate the URL, thereby redirecting users to a webpage under the adversary’s control. This manipulation potentially facilitates actions such as:
https://legitwebsite.tld/login.html?redirect_to=https://phishingwebpage.tld
Although this vulnerability isn’t new with the arising of new security technologies, mainly in the Email Security Gateways (ESG) area, its exploration is having a major increase and impact by threat actors trying to attempt to bypass them.
Campaign Overview
Over the past few months, ArtResilia Security Operations Center (SOC) has observed a notable surge in phishing campaigns centering around Business Email Compromise (BEC) incidents. These campaigns exploit legitimate websites and platforms by utilizing URL redirects to lead users to malicious pages. A comprehensive examination of historical data substantiated this recurring trend, allowing us to pinpoint instances where various types of platforms were exploited. Notably, this encompassed the misuse of social networking platforms, search engines, news websites, and even platforms with security-related purposes.
Since the start of the year, there has been a significant and prominent upsurge, evident not only in the volume of campaigns (as depicted in the left chart) but also in the volume of abused websites as illustrated in the right chart.
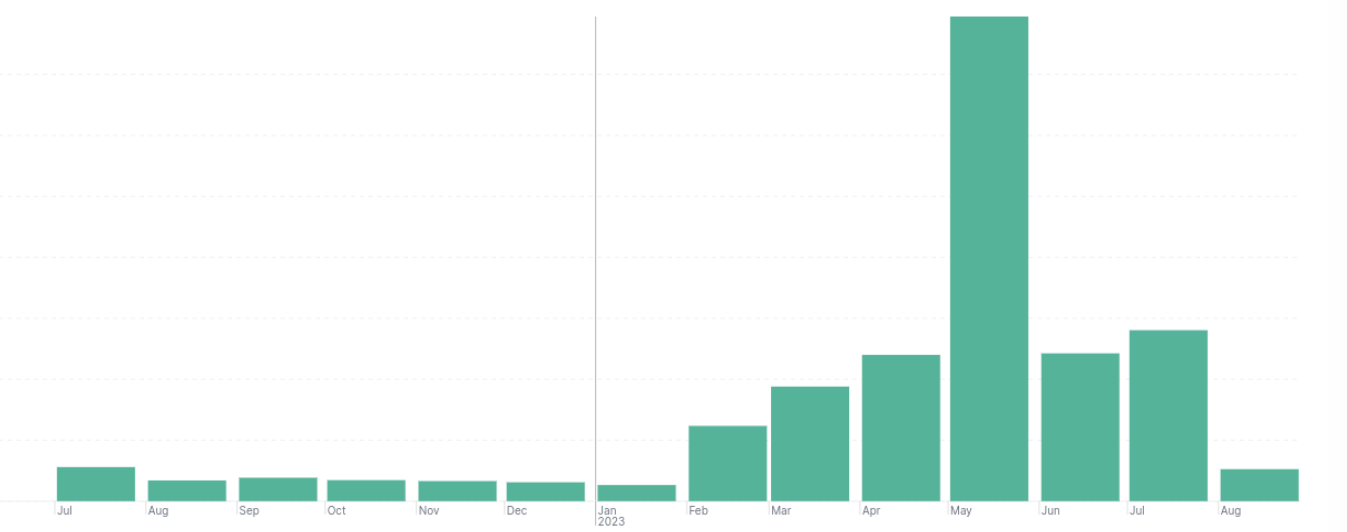
Figure 1: Figure 1: Campaigns over time and with the highest volume of abuse in May 2023.
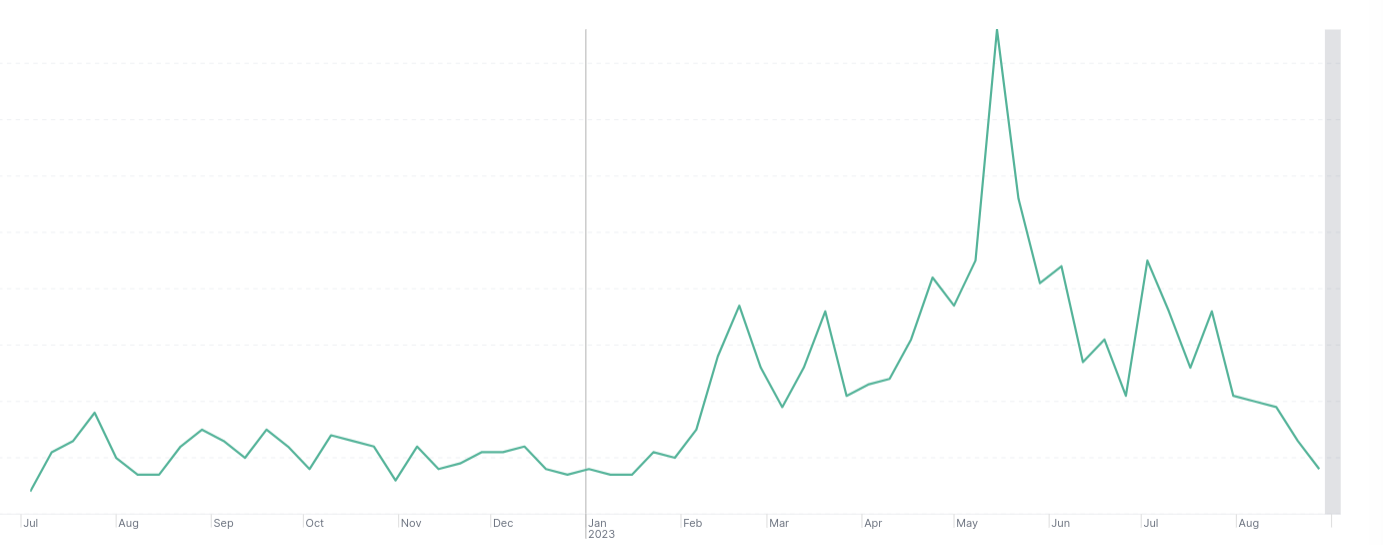
Figure 2: Abused websites fully correlated with the volume of abuses observed in the graph in Figure 1.
Results
In total, we have identified more than 200 single websites/domains used to distribute these kinds of campaigns. This trend strongly suggests that threat actors are increasingly adopting this technique as a means to circumvent Phishing and Spam Filters. The rationale behind this scenario is that the primary URL often appears authentic within a business context.
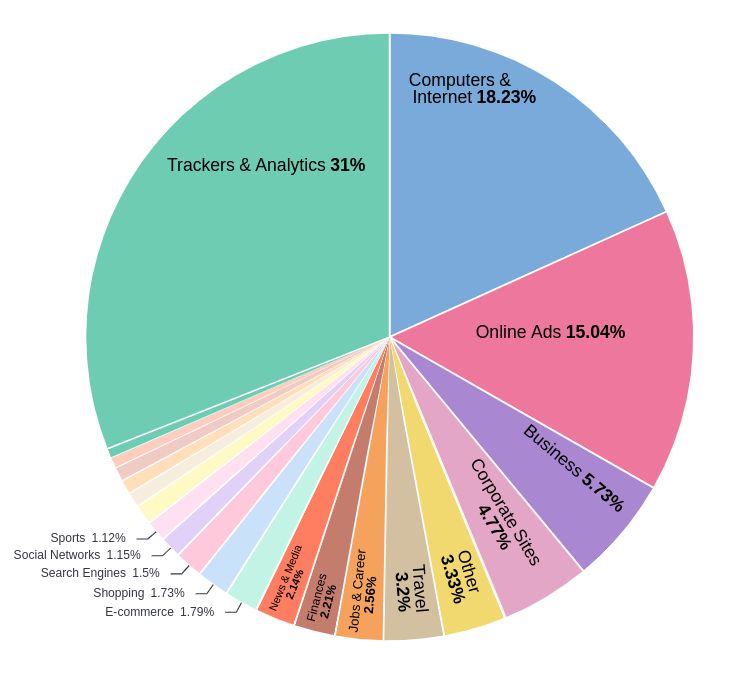
Figure 3: Abused websites category distribution.
The following chart shows that most of the abused platforms are related to Marketing and Advertising platforms, but it was also possible to identify the exploration of existing vulnerabilities in websites associated with other business sectors like Computers & Internet, Traveling, or News and Media.
Some of these platforms are in the top 1000 of CloudFlare domain ranking Radar and more than 20 websites were even in the top 1K Cisco’s Umbrella ranking at the time of this analysis.
Another curious pattern of using the same website being abused in multiple campaigns over time was also observed in campaigns using multiple abused platforms. The heatmap below demonstrates a correlation between the most commonly abused websites and the final landing page.
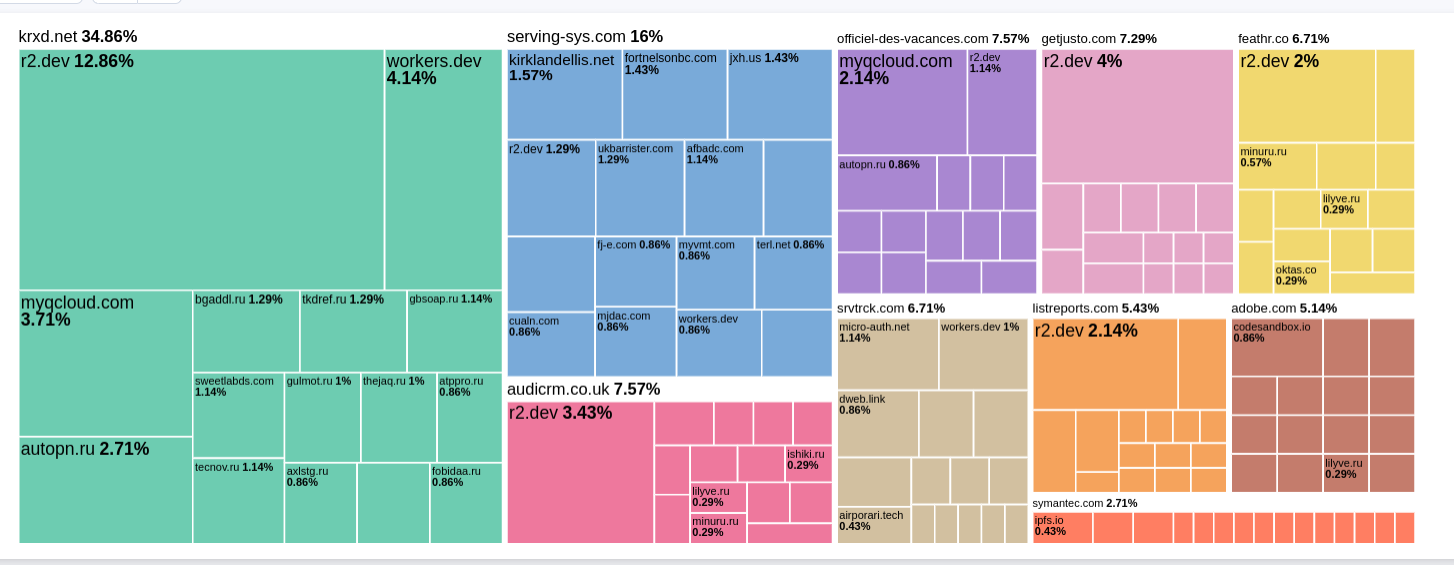
Figure 4: Correlation between abused platforms and campaigns (2022 and 2023).
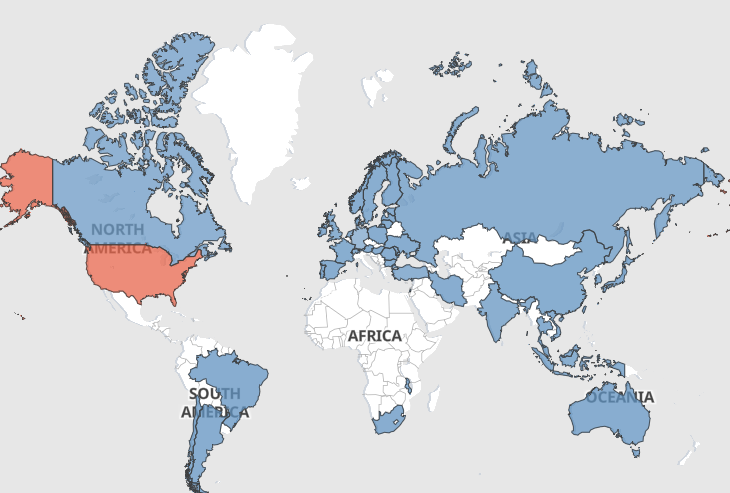
This investigation also confirmed other patterns that were seen more frequently. In detail, threat actors are adopting a strategy wherein they conceal and host their Phishing Kits within Content Delivery Networks (CDNs), often leveraging Cloudflare as a protective layer, with most of these services hosted in the United States of America. This observation underscores that solely relying on Geolocation policies possesses constrained efficacy in countering these tactics.
 |
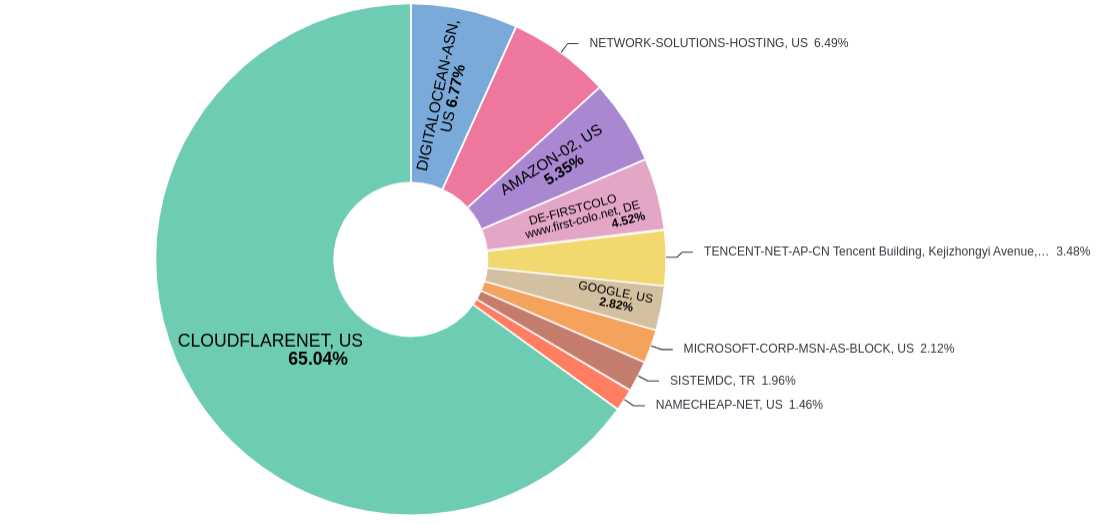 |
Figure 5: ASN of Phishing Pages and Geo Location.
Conclusions and Recommended Actions
This analysis allowed us to identify a high number of platforms used to hide malicious campaigns and bypass ESG technologies. The abuse of business legit platforms creates a new challenge to Phishing/Spam Technologies but also to the SOC and IT teams that want to protect their users. Even if the final page is considered malicious, abusing these techniques permits in some cases to bypass the first layer of protection. The decision of security vendors like Microsoft, in blocking these platforms/domains or considering them as unsafe is difficult as they may impact legitimate businesses.
There is no magic solution that could solve this problem. On one side we have companies that own these websites and should put in place some best practices like (i) rigorous input validation and whitelisting techniques ensuring that only legitimate URLs are permitted, (ii) parameter sanitization is crucial to eliminate malicious characters and payloads from the URLs, and (iii), logging to ensure traceability and accountability of potential abusers.
In another perspective and to defend against attacks abusing this technique, Blue Teams can perform retro hunting activities in SIEM, Proxy Logs, or Data Lakes to identify received campaigns and possibly identify past compromised accounts.
For example, this query developed in our SOC can be executed in Advance Hunting included in Microsoft Security Suite and It will aggregate the URLs contained in emails grouping by the primary domain and the secondary domain contained in the URL.
////Author Sergio Ribeiro - artresilia.com
let trusted_domains = datatable (domain: string)
[
"mydomain.tld", //Exclude the domains that you consider safe
"myemailmarketingplatform.tld", //Exclude the domains that you consider safe
];
DeviceEvents
| where RemoteUrl matches regex @"https*://.*\=https*://"
| extend domains=extract_all(@"https*://((?:[a-z0-9](?:[a-z0-9-]{0,61}[a-z0-9])?\.)+[a-z0-9][a-z0-9-]{0,61}[a-z0-9])", RemoteUrl)
| where tostring(domains[0]) != tostring(domains[1]) and tostring(domains[0]) !in (trusted_domains)
| summarize by tostring(domains)
Another version excluding trusted senders a grouping the original domain with the sender:
//Author Sergio Ribeiro - artresilia.com
let trusted_domains = datatable (domain: string)
[
"mydomain.tld", //Exclude the domains that you consider safe
"myemailmarketingplatform.tld", //Exclude the domains that you consider safe
];
let trusted_senders = datatable (domain: string)
[
"[email protected]", //Exclude the senders that you consider safe
];
EmailUrlInfo
| join kind=inner EmailEvents on NetworkMessageId
| where Url matches regex @"https*://.*\=https*://" and UrlDomain !in (trusted_domains) and SenderFromAddress !in (trusted_senders)
| extend domains=extract_all(@"https*://((?:[a-z0-9](?:[a-z0-9-]{0,61}[a-z0-9])?\.)+[a-z0-9][a-z0-9-]{0,61}[a-z0-9])", Url)
| where tostring(domains[0]) != tostring(domains[1])
| summarize count() by tostring(domains[0]), SenderFromAddress
A similar one but It will look for the EDR events mainly traffic of the endpoints.
let trusted_domains = datatable (domain: string)
[
"mydomain.tld", //Exclude the domains that you consider safe
"myemailmarketingplatform.tld", //Exclude the domains that you consider safe
];
DeviceEvents
| where RemoteUrl matches regex @"https*://.*\=https*://"
| extend domains=extract_all(@"https*://((?:[a-z0-9](?:[a-z0-9-]{0,61}[a-z0-9])?\.)+[a-z0-9][a-z0-9-]{0,61}[a-z0-9])", RemoteUrl)
| where tostring(domains[0]) != tostring(domains[1]) and tostring(domains[0]) !in (trusted_domains)
| summarize by tostring(domains)
These queries will identify which emails and addresses were used in the organization, matching the pattern of URL redirection with a high level of confidence. The results should then be analyzed and the query tailored to exclude false positives from your baseline. Then use the triaged list in your Proxy, EGS, SafeLinks, Edr, etc. to block connection attempts to the initial redirector.
We also provide a list of the top domains that we detected as being abused in recent times and we suggest blocking e-mail messages with hyperlinks where they are present in your mail gateway/spam filter and if possible in your Firewall/Proxy. However, the usage of this list should be evaluated across your organizational context as it may impact some legit business activities and therefore use it at your own risk.
apiservices[.]krxd[.]net
bs[.]serving-sys[.]com
links[.]marketing[.]audicrm[.]co[.]uk
eulerian[.]officiel-des-vacances[.]com
api[.]getjusto[.]com
polo[.]feathr[.]co
r[.]srvtrck[.]com
adclick[.]g[.]doubleclick[.]net
e[.]targito[.]com
secure[.]adnxs[.]com
www[.]listreports[.]com
l[.]wl[.]co
Enforcing Multi-Factor Authentication (MFA) and strong authentication methods for users stands as an imperative and non-negotiable measure. In addition, vigilant monitoring for the creation and approval of newly requested OAuth applications emerges as a vital practice to adopt. Furthermore, the introduction of a comprehensive awareness program is deemed mandatory to improve the overall security posture.
Author