With the high wave of attacks that have been witnessed in recent times, the increased capabilities of malicious actors and the regulations implemented globally, many organizations have not yet managed to implement all the necessary policies in order to meet all the legal requirements imposed these days. Not only focusing on the fact of compliance with the current laws, it is important to realize that the main purpose of these laws is to help in the protection of personal data, a vital target for maintaining a safer world with privacy.
Throughout this article, we will address the General Data Protection Regulation (GDPR), a mandatory regulation, and the ISO/IEC 27001:2022 framework, pointing out how we can use the synergies of the two in parallel to build a robust and resilient internal information security framework in an organization.

General Data Protection Regulation
The General Data Protection Regulation is a comprehensive data protection law that was implemented by the European Union (EU) in May 2018 with the primary goal of improving the protection of individuals’ personal data and giving them more control over how their data is collected, processed, and used by organizations.
The right to be informed, the right to access their data, the right to correct inaccurate data, the right to erasure (or “right to be forgotten”), the right to restrict processing, the right to data portability, and the right to object to processing are some of the rights that the GDPR seeks to strengthen for individuals.
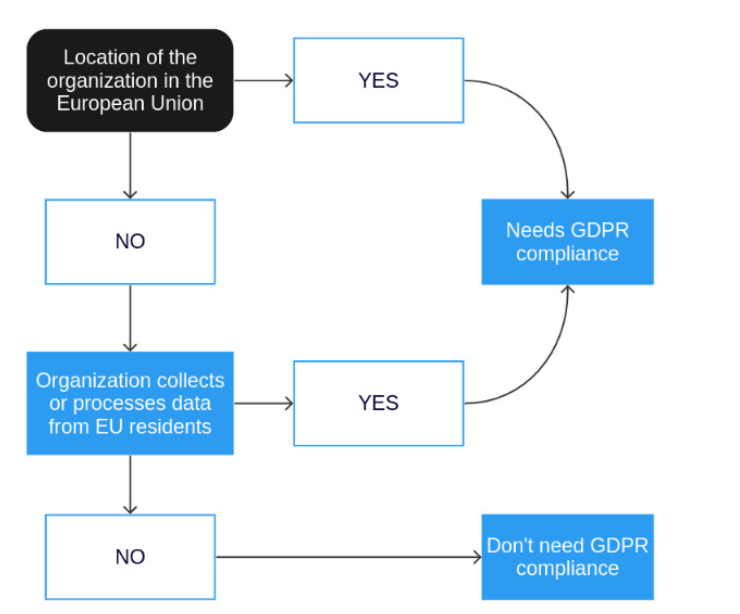
Who Needs To Comply with GDPR
Regarding who needs to comply with GDPR regulations, the diagram below shows in a simple way how to figure out whether your organization does or not. Basically, any organization that collects or processes data from citizens residing in the European Union needs to be GDPR compliant.
ISO/IEC 27001
ISO/IEC 27001, also known as ISO/IEC 27001:2013 or ISO/IEC 27001:2022 (new version), is an international standard (well recognized) for information security management systems (ISMS). It offers businesses a methodical and risk-based approach to managing and safeguarding their information assets, including private information, proprietary information, and consumer data. The primary goal of the ISO/IEC 27001 is to assist businesses in establishing, implementing, monitoring, and continuously improving an effective ISMS to guarantee the availability, confidentiality, and integrity of their information assets.
The standard includes specifications for risk analysis and management, information security policies, organizational controls, access control, asset management, encryption, physical and environmental security, communications security, operations security, and more.
ISO/IEC 27001 Controls
ISO/IEC 27001 (2022) is based on four domains with multiple controls within each domain. The list below identifies all of these domains, while further down in the post identifies the controls that have the capability to help with GDPR compliance.
- People (8 controls)
- Organizational (37 controls)
- Technological (34 controls)
- Physical (14 Controls)
Compliance vs Volunteering
Both GDPR and ISO/IEC 27001 provide firm foundations for establishing and upholding reliable data protection processes. While ISO/IEC 27001 is a voluntary standard that offers a methodical method for controlling information security risks, GDPR is a legal requirement.
A set of safeguards to protect sensitive information and personal data are outlined in the GDPR regulation and ISO/IEC 27001 standards. Organizations are required to abide by the GDPR’s multiple data protection principles, including data minimization, purpose limitation, and accountability.
Organizations must comply with GDPR requirements to engage with regulatory authorities and submit to data protection audits. To get and keep certification under ISO/IEC 27001, enterprises must submit to internal and external audits by certified authorities.
Despite the fact that ISO/IEC 27001 is a voluntary standard for information security management and GDPR is a legal regulation focusing on data protection, both have common requirements and principles relating to risk-based approach, documentation, data protection controls, continuous improvement, accountability, third-party management, and compliance verification.
Organizations may take advantage of the synergies between GDPR and ISO/IEC 27001 to build a strong and resilient framework for information security and data protection that complies with industry standards and legal regulations.
Synergies
Once the organization chooses to implement the ISO 27001 framework the compliance with the ISO Annex A controls is inevitable, but that is not the same as ensuring compliance with GDPR. As said before the ISO 27001 provides a framework for establishing an ISMS and its optional, on other hand the GDPR is a regulatory requirement that organizations must adhere to when processing personal data of individuals. Before discussing the Annex A controls and their connections to GDPR there is an important disclaimer to be made, not all the mentioned controls have references directly to GDPR or any specific GDPR regulation, but all of them in some dimension help the organizations to get closer to GDPR requirements and its requirement practices.
Below is an overview of each of these controls, their definition and the link between the ISO 27001 framework and the GDPR:
A.5.1 – Policies for Information Security – This control is indexed directly with article 32 and article 24 of GDPR which outlines the necessity of the organizations to implement various levels of security in order to protect personal data information. The article 24 clearly states that the measures of protection include the application of policies in the matter of data protection.
A.5.3 – Segregation of Duties – Defining specific roles and responsibilities across an organization helps to reduce any opportunity for unauthorized or unintentional modification and misuse of data, with that, maintaining data integrity, and enabling data controllers to determine who is responsible for a specific data, thereby achieving accountability, one of the indirect dimensions of GDPR.
A.5.31 – Legal, Statutory, Regulatory and Contractual Requirements – When implementing this control, organizations inside the European Union need to identify and document the GDPR as a primary piece of applicable legislation. This involves understanding the requirements of the GDPR, such as the data protection principles, individuals’ rights, lawful bases for processing, data breach notification obligations, and cross-border data transfer rules.
A.5.5 – Contact With Authorities – One of the dimensions of data controllers checklist in the GDPR is that the organization must have in place procedures to notify authorities in case of data breach, so this ISO 27001 control is exactly that, implement communication channels with relevant authorities not just police enforcement but also sector regulatory bodies, supervisory authorities or any other relevant authority figure, and that is clearly mentioned on GDPR article 33.
Important to mention the article 36 of GDPR which gives guidelines that in certain situations, organizations must consult with the supervisory authority before carrying out processing activities that are likely to result in high risk to data subject’s rights and freedoms.
A.5.9 – Inventory of Information and Other Associated Assets – By maintaining an inventory of information assets up-to-date is crucial for this synergy, understanding the types of personal data which is stored, processed or transmitted is essential to fulfill the GDPR requirements because knowing the information that the organization has is the first step to know what it has to protect.
A.5.10: Acceptable Use of Information and Other Associated Assets – This control is connected to GDPR Article 5, which emphasizes the principle of integrity and confidentiality, as it requires establishing rules for the acceptable use of information and assets associated with personal data.
A.5.15 – Access Control – This control is directly connected to article 32 of GDPR, that by establishing a robust and well structured access control policy the organizations align with the GDPR principle of ensuring appropriate security measures for personal data. By implementing effective access controls such as the segregation of access, defining user privileges and monitoring access activities applying the principles of least privilege and the need-to-know, organizations can control and protect the access to personal data.
A.6.1: Screening – This control is connected in some dimensions to GDPR Article 6 and Article 30, as it requires conducting background verification checks on candidates for employment, which helps ensure the suitability and trustworthiness of individuals who may have access to personal data.
A.8.1 – User Endpoint Devices – Given the ever-evolving corporate culture and the increasing necessity to transfer and handle data outside office premises, it becomes crucial to establish a robust mobile device policy. This policy addresses various control dimensions such as the registration of mobile devices, requirements for physical protection, and restrictions on software installation.
Additionally, the policy outlines specifications for mobile device software, restrictions on connections, and the utilization of cryptographic techniques. By incorporating these measures, organizations can effectively enforce personal data protection protocols and ensure compliance with Article 32 of the GDPR.
Article 32 mandates organizations to implement suitable technical and organizational measures to safeguard personal data. These measures must consider factors such as technological advancements, implementation costs, and the nature, scope, context, and purposes of data processing. Thus, a comprehensive mobile device policy not only enhances data protection but also aids in regulatory compliance and cybersecurity.
A.8.8 – Technical Vulnerability Management – This control is connected to GDPR Article 32, as it emphasizes the need for regular technical vulnerability assessments and patch management to protect personal data from potential security vulnerabilities.
8.11 – Data Masking – Data masking aligns with GDPR’s encouragement of pseudonymization techniques to protect personal data. It involves altering or disguising sensitive information, similar to pseudonymization, making it unintelligible to unauthorized individuals.
8.12 – Data Leakage Prevention – It’s a strategy or set of tools and processes designed to ensure that sensitive data is not lost, misused, accessed by unauthorized users, or leaked outside the organization’s secure environment. Implementing DLP measures aligns with fundamental GDPR principles, particularly Article 5, emphasizing data integrity and confidentiality. These measures also directly support Article 32 by fortifying security measures against unauthorized data access or disclosure, thereby enhancing compliance with GDPR’s security requirements. By proactively implementing and maintaining strong DLP strategies, organizations mitigate the likelihood and impact of potential data breaches, ensuring adherence to GDPR’s stringent data protection standards while safeguarding personal data integrity and confidentiality.
A.8.15 – Logging – Implementing event logging and mechanisms for auditing the log records help organizations to detect any security events, by monitoring and tracking any kind of accesses to personal data or even support investigations after an incident, the control does not mention GDPR directly but helps demonstrating compliance with GDPR’s accountability principle.
A.8.24 – Use of Cryptography – One of the GDPR’s requirements (article 32) is that every personal data whenever possible should be encrypted, pseudonymised or anonymised. The ISO/IEC 27001 framework addresses this regulation requirement through this control of Annex A which states that a cryptographic policy should be developed. This control also has a particular guideline for data protection and states that the objectives of this implementation are very clear and outlines 4 main objectives of protection:
- Confidentiality: Encryption to protect unauthorized access;
- Integrity/Authenticity: so ensure the veracity of data and that remains reliable
- Non-Repudiation: using cryptographic techniques to provide evidence of the occurrence or non occurrence of an event in order to ensure accountability;
- Authentication: Cryptographic techniques for authentication for users or systems that request access or transactions.
Given that personal data is highly valuable and that GDPR imposes significant fines for data breaches, the proper implementation of this control and of a policy dedicated to cryptography helps the organizations reaching accountability in a way that the policy states all roles and responsibilities must be outlined, all information assets must be identified and classified, and appropriate cryptographic controls must be implemented based on the level of risk associated with each asset. This policy ensures that the organization establishes clear guidelines and procedures for the secure use of cryptographic techniques, including key management, encryption algorithms, and secure storage of cryptographic keys.
A.8.25: Secure Development Lifecycle – This control is connected to GDPR Article 25, as it encourages the adoption of secure development practices to ensure that privacy and security are considered throughout the development lifecycle of systems and applications handling personal data.
Important Note
It is crucial to remember that, while ISO/IEC 27001 offers a framework for developing information security measures that can assist GDPR compliance, it does not ensure full GDPR compliance and controls alone are not sufficient for full GDPR compliance. Organizations must consider additional measures specific to GDPR, such as conducting data protection impact assessments (DPIAs) or appointing a data protection officer (DPO), in order to guarantee complete compliance with the legislation. Organizations must continue to carefully analyze and assess their data processing methods and processes against the GDPR’s precise requirements, and seek legal guidance if required.
If you need support in implementing ISO/IEC 27001, Art Resilia has a specialized team to support its implementation. Email us for more information: [email protected]
References
GDPR Compliance Checklist – GDPR.eu
Guidelines, Recommendations, Best Practices | European Data Protection Board
ISO/IEC 27001 Standard – Information Security Management Systems
EU GDPR & ISO 27001 Integrated Documentation Toolkit | Advisera
Authors
Bernardo Rodrigues & Luís Gonçalves