Demystifying GraphQL Introspection: Risks, Visualization and Analysis
GraphQL has revolutionized how APIs are designed and consumed, offering flexibility and efficiency in data fetching. One of the key features of GraphQL is Introspection, which allows clients to query the schema and discover the available types, fields, and operations. While introspection is a powerful tool for development and debugging, it’s crucial to understand its implications and ensure it is disabled in production environments.
What is GraphQL Introspection?
GraphQL introspection is a mechanism that enables clients to query the schema itself. It allows clients to retrieve detailed information about the available types, their fields, and the operations that can be performed. This feature is incredibly useful during development and debugging, as it helps developers understand and interact with the API schema.
Introspection queries typically involve querying the __schema and __type objects, which are built into every GraphQL schema. These queries can provide information about query types, mutations, input types, and more.
You can read more about Introspection on GraphQL’s official documentation here.
The Risks of Enabling Introspection in Production
While GraphQL introspection is a powerful tool during development, it should never be enabled in production environments. Enabling introspection in production poses significant security risks:
- Exposing Sensitive Information: Introspection allows anyone with access to the GraphQL endpoint to explore the schema’s structure. This includes potentially sensitive information about your data models, operations, and types.
- Schema Enumeration: Attackers can use introspection to discover vulnerabilities in your schema, including finding unused or deprecated fields that may be exploitable.
- Query Complexity Attacks: Introspection can be used to analyze query complexity and depth, which can help attackers craft malicious queries designed to overload your server.
To mitigate these risks, GraphQL Introspection should be disabled in production environments. You can achieve this by configuring your GraphQL server to reject Introspection queries or by setting up middleware to handle Introspection requests differently.
Visualize Introspection Data with GraphQL Voyager
GraphQL Voyager is an open-source tool that provides a graphical representation of GraphQL schema. It offers an interactive, node-based diagram that allows to explore the schema’s types, fields, and relationships visually.

Local Installation (Open-Source)
GitHub: You can find the GraphQL Voyager GitHub repository at https://github.com/graphql-kit/graphql-voyager. Follow the installation and setup instructions provided in the repository’s README to set up GraphQL Voyager in your project.
Using GraphQL Voyager Online
Web Service: If you prefer not to install GraphQL Voyager locally or want a quick way to explore your schema without any setup, we can use the online service provided at https://graphql-kit.com/graphql-voyager/. This web-based version of GraphQL Voyager allows us to upload our introspection query result to visualize our schema instantly.
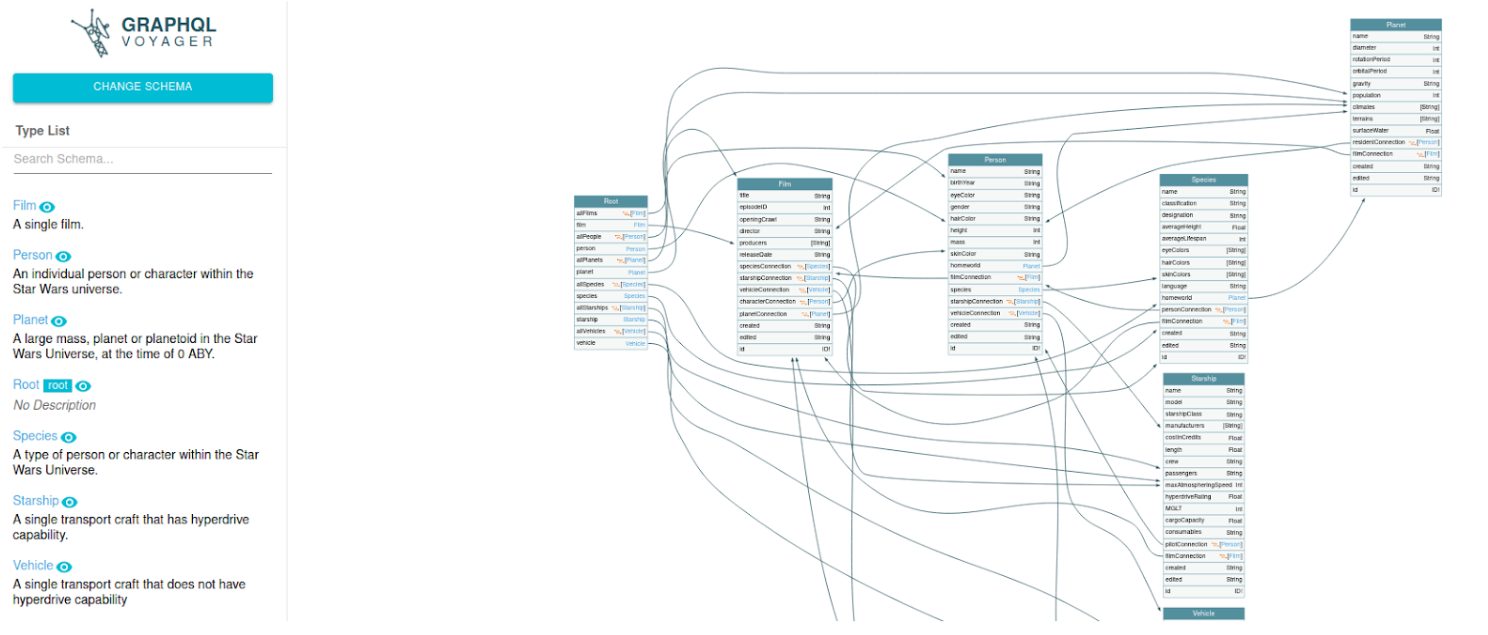
This tool enables us to navigate the schema, inspect types, fields, and relationships, and uncover potentially overlooked attack vectors. By exploring the GraphQL schema visually, we can identify hidden data paths, pinpoint deprecated fields that might be exploitable, and assess query complexity, all of which are essential for a thorough security assessment.
Demo Example
To see how it all works, we’ll use a demo available on the web at https://graphql-demo.mead.io/.
We will use the Introspection query to acquire the entire GraphQL schema for this host. Introspection query:
{__schema{queryType{name}mutationType{name}subscriptionType{name}types{...FullType}directives{name description locations args{...InputValue}}}}fragment FullType on __Type{kind name description fields(includeDeprecated:true){name description args{...InputValue}type{...TypeRef}isDeprecated deprecationReason}inputFields{...InputValue}interfaces{...TypeRef}enumValues(includeDeprecated:true){name description isDeprecated deprecationReason}possibleTypes{...TypeRef}}fragment InputValue on __InputValue{name description type{...TypeRef}defaultValue}fragment TypeRef on __Type{kind name ofType{kind name ofType{kind name ofType{kind name ofType{kind name ofType{kind name ofType{kind name ofType{kind name}}}}}}}}
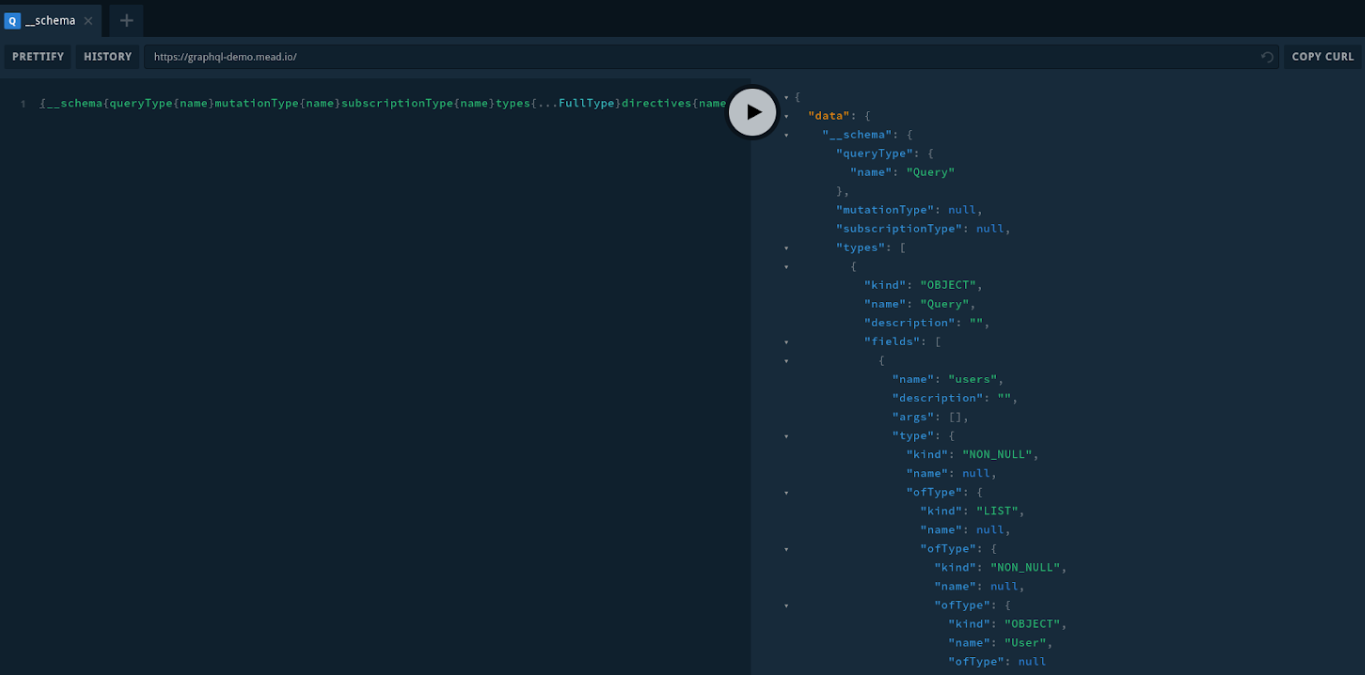
Next, we’ll copy the entire response and paste on GraphQL Voyager:
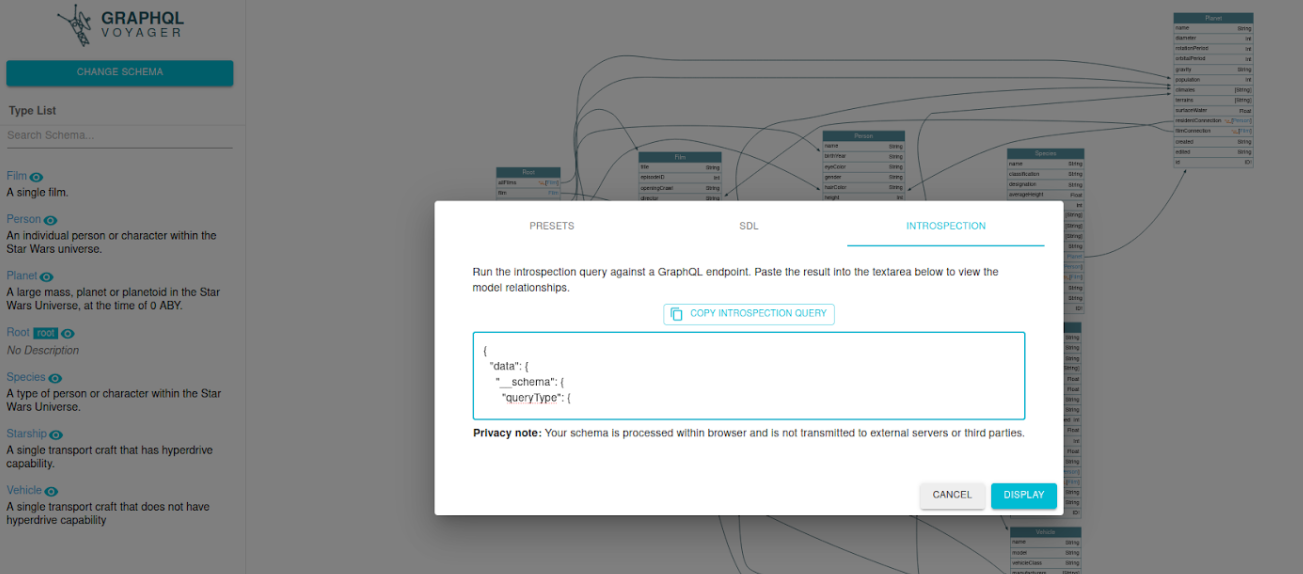
After making the “Display”, we will get the graphic information from the Introspection and we will have the various interconnections between the different objects:
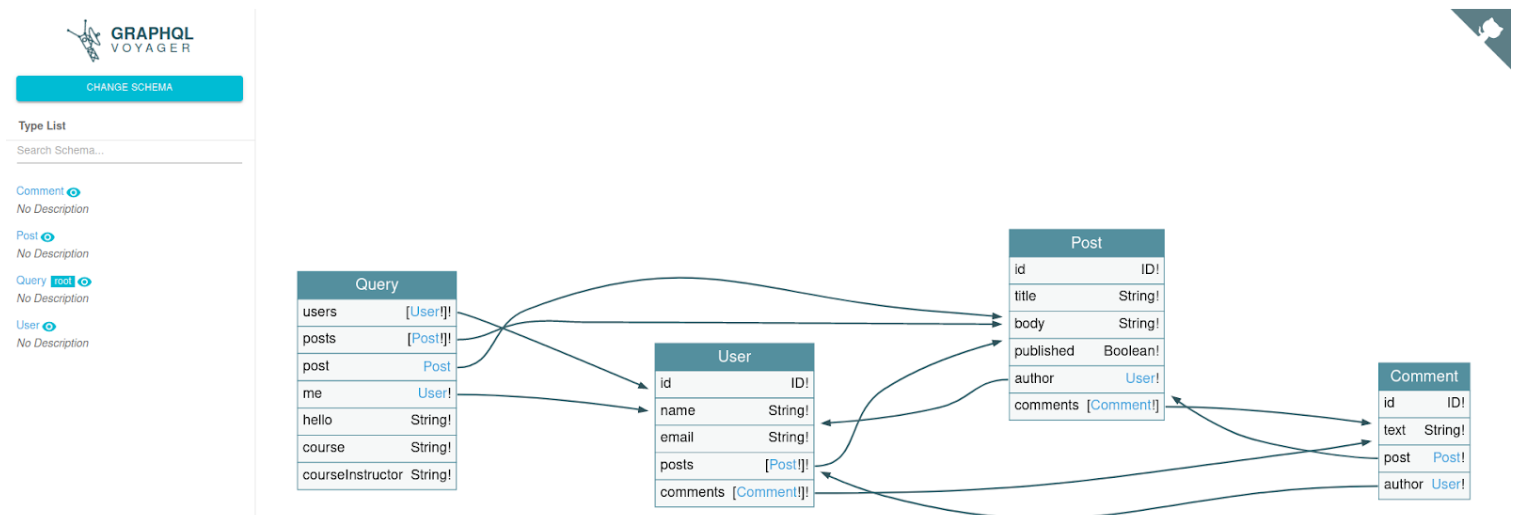
One of the great advantages of this service is that we can use the search field to filter by what we want to look for, and we can also search within objects. With this, we can easily search for highly important information, such as whether an object invokes the password field, for example.
Analyze Introspection Data using Postman
Postman is a versatile and powerful API development and testing tool that enables developers and testers to streamline the process of working with APIs. Much like tools such as Burp Suite, Postman offers a user-friendly interface for designing, testing, and documenting APIs. It allows users to send HTTP requests to APIs, inspect responses, and automate various aspects of the testing and integration process. This makes it an good resource for developers, quality assurance professionals or security auditors when it comes to ensuring the functionality, reliability and security of APIs in today’s interconnected software ecosystem.
Using Postman for GraphQL queries
Postman now has the ability to execute GraphQL queries more easily in its service, being able to automatically search for the existence of active Introspection. To do this, start a new project by clicking on the “GraphQL” button.
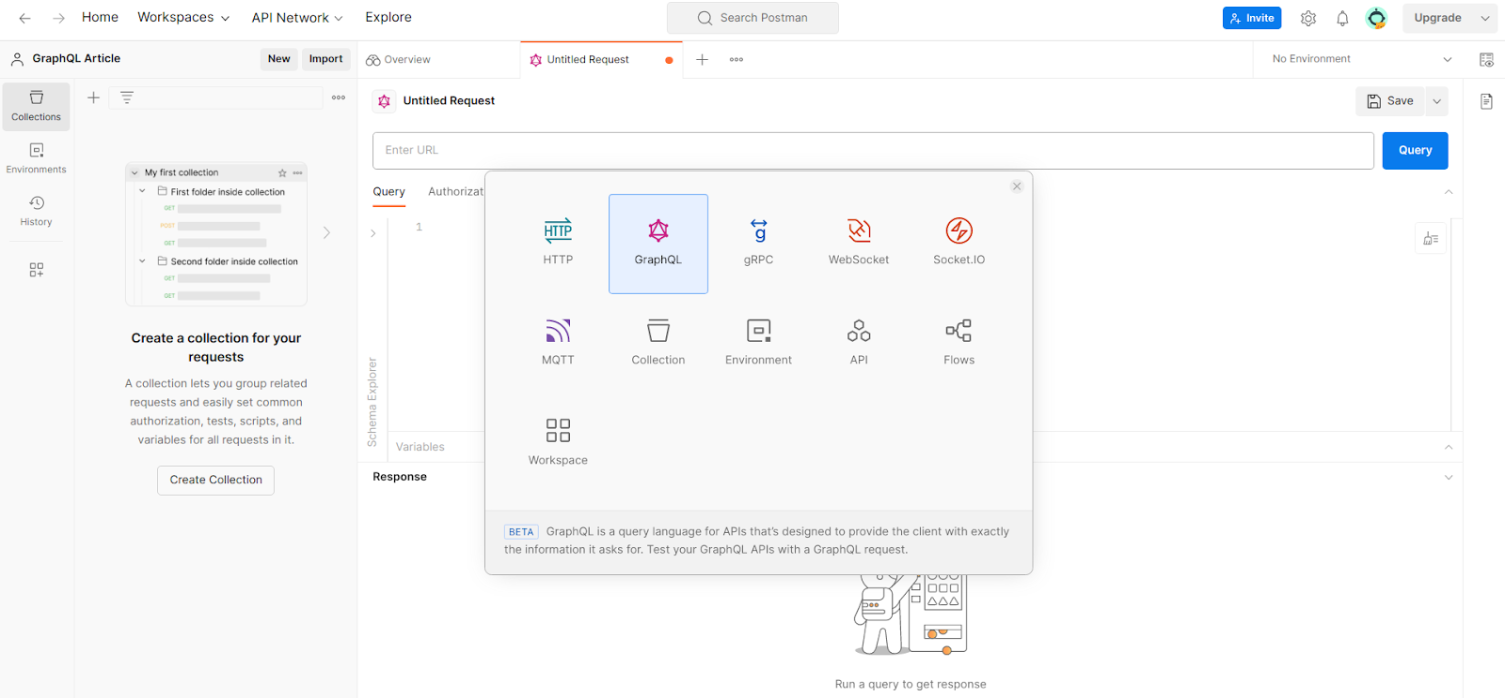
When we insert the link in the URL box identified in the image below, Postman automatically tries to run the Introspection, automatically obtaining the data if Introspection is active in the application to be audited.
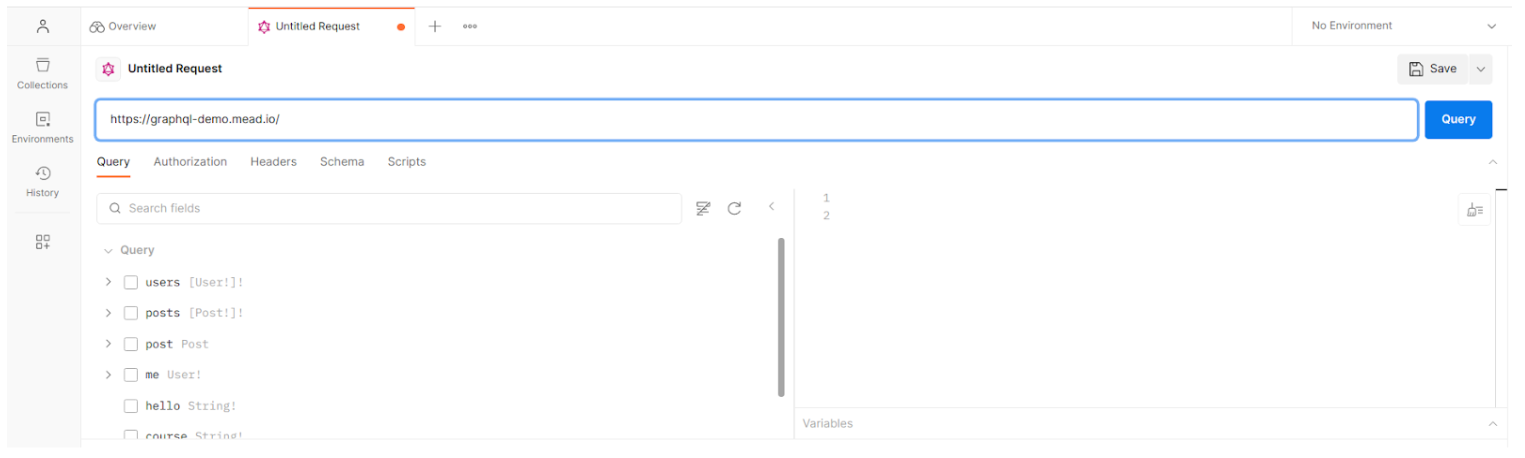
As we can see in the image above, queries have been generated for the different existing objects on the Query tab.
From that moment on, everything becomes simpler. All you have to do is select the query you want to execute and execute the POST query. If authentication is required, use the “Authorization” tab, which already contains some authentication methods such as Bearer or OAuth, which must be filled in with the respective session token.
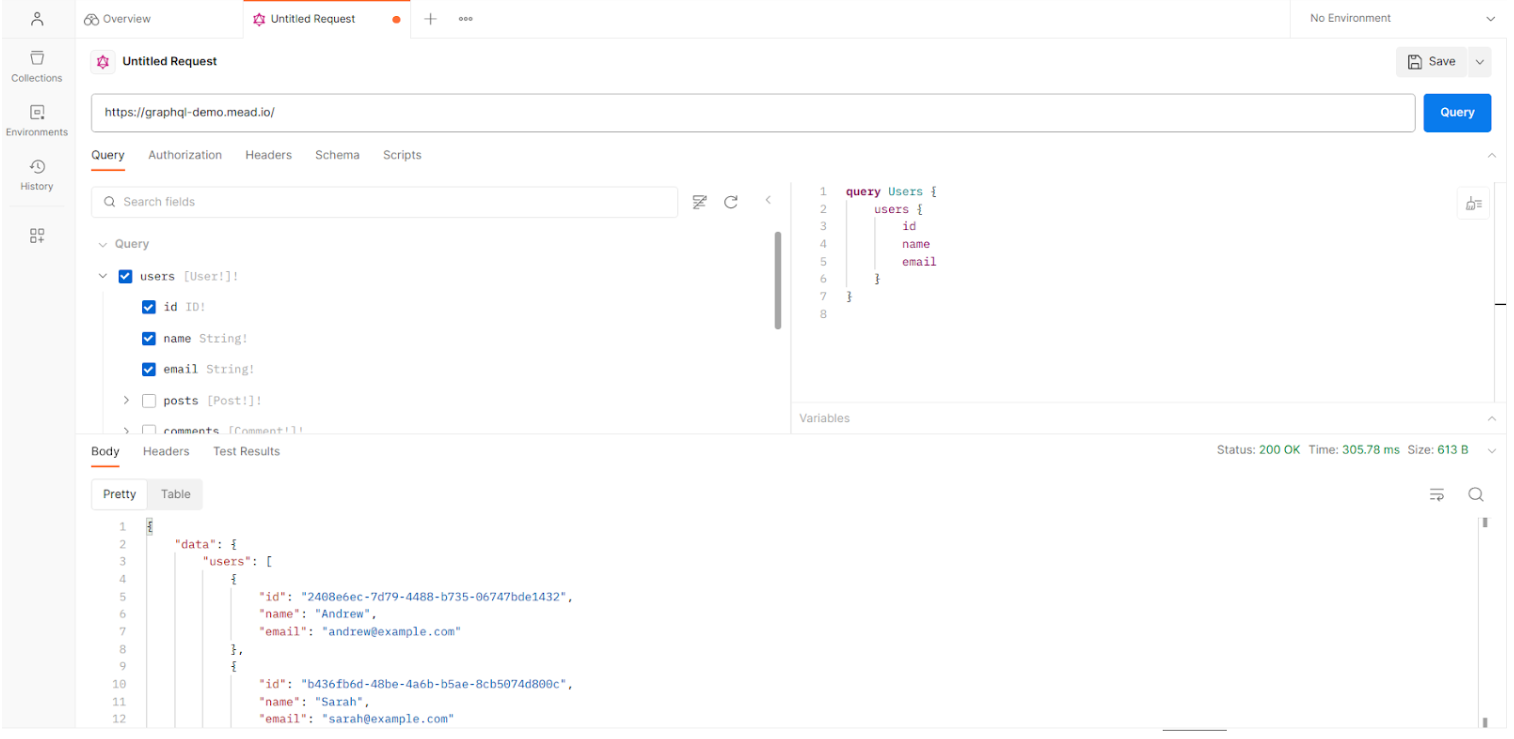
By using GraphQL Voyager to analyze the interconnections between objects and make searches that easily identify critical fields, we can more quickly identify queries that should be reviewed with greater emphasis, and with Postman quickly move on to the process of executing those same queries seen earlier and obtain the respective response data.
Conclusions
GraphQL Introspection is a powerful feature that should be used with caution. While it’s invaluable for development and debugging, enabling it in production can introduce serious security risks. Always remember to disable introspection in your production environment to protect your API.
To make the most of Introspection data for development purposes, tools like GraphQL Voyager can be incredibly helpful. They provide a visual representation of your schema, making it easier to understand and navigate the complex world of GraphQL APIs. Postman offers a light and easy-to-use service, and the combination of these two is a great starting point for analyzing GraphQL schemes.
In summary, GraphQL Introspection is a double-edged sword. Use it wisely during development, and make sure it’s sheathed when your GraphQL API goes into production.
Author