Secure Networks: (Un)Secure Protocols | EP 1
Networks are fundamental in any organization regardless of the industry they are in. They allow the entire flow of the organization to run and promote the connection between different departments or units.
Depending on the size of each organization, managing an internal network can be highly challenging and requires changes to be made regularly and often compromises must be made. In addition to the need for a fully functioning network, which can be difficult to achieve in highly heterogeneous networks, it is important to reconcile it with the ever-increasing need for higher network environment resilience.
With the recent increase in where cyber-attacks are occurring, we have observed that not always the best mechanisms or care have been put in place on the affected network, leading to catastrophic losses for successfully attacked organizations.
Again, it is noteworthy to mention how difficult it can be to control an internal network and implement all the cyber security capabilities at each location. That’s why in this series of episodes – Secure Networks – we’ll talk about some good ways to manage the network, as well as implementations that aim to increase the security and resiliency of the network environment.
Starting With The Protocols
Network protocols are like a language between devices utilized to transmit, receive, and process information. These protocols establish rules to define how information is transmitted between devices. There are several network protocols, each with its function, nonetheless, many of these protocols are considered insecure and alternatives to them must be implemented.
Not-so-secure Protocols
The usage of a wide range of network protocols is a clear sign of the fast growth of technology in recent years. Many of them are not as secure as expected leading to the exploration of classic and popular vulnerabilities and putting the network at continuous risk. For the most part, their inability to provide authenticity, integrity, or confidentiality makes them a liability.
Some of the network protocols with popular flaws are:
- SMBv1/v2
-
-
- Sharing access to files, printers, serial ports, and other network resources is made possible through the client-server communication mechanism known as the Server Message Block (SMB) protocol.
-
- HTTP
-
-
- In the Internet protocol suite concept, the Hypertext Transfer Protocol (HTTP) is an application layer protocol, serving as a web server.
-
- Telnet
-
-
- A command line interface for communicating with a remote device or server is provided via the protocol known as Telnet.
-
- SNMPv1/v2
-
-
- The network protocol Simple Network Management Protocol (SNMP) is used in Internet Protocol networks to manage and keep track of network-connected devices.
-
- FTP
-
-
- The network protocol called FTP (File Transfer Protocol) is used to transfer files between computers using TCP/IP (Transmission Control Protocol/Internet Protocol).
-
- LLMNR
-
- LLMNR (Link-Local Multicast Name Resolution) is a protocol that comes enabled by default on Windows systems, working for name resolution over IPv4 and IPv6.
These are just a few examples of protocols that are insecure and mostly found on internal networks. Most of these protocols send information in plain text, making it easy for network sniffing purposes and obtaining information transmitted by them, including credentials. As for SMBv1/v2, it contains exploitable flaws used for lateral movement scenarios in a network compromised by malicious actors.
Secure Network Protocols
Now we have seen some examples of insecure protocols, it is important to consider their alternatives and the need for their implementation for greater security both on devices and on internal networks.
- SMBv1/v2 => SMBv3
- HTTP => HTTPS
- Telnet => SSH
- SNMPv1/v2 => SNMPv3
- FTP => SFTP (Implemented by SSH)
- LLMNR => DNS
These protocols meet the requirements concerning authenticity, integrity, and confidentiality depending on the needed conditions.
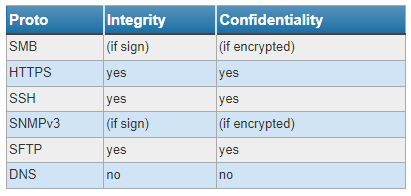
With this upgrade from the network level point of view, we are only making the communications of these protocols more secure and fixing some known vulnerabilities, but not changing the systems’ features.
Implementation of Secure Protocols
Implementing the most secure protocols is not always easy because of the different types of devices on the network and their need for certain protocols. In fact, this is seen as a big challenge on legacy networks. In that way, internal audits must be a valuable process in order to understand how to implement better security on devices, decommission the use of legacy protocols if possible, and even spotlight potential risks of these devices for the security of the entire infrastructure.
Given the wide range of companies that use Active Directory, a simple way to implement these protocols globally could be the usage of Group Policies.
Another important part of the slice is developers and users in general. These have a fundamental role in this new paradigm and should be educated about the dangers and good practices of this digital era and mainly focusing on the use of external devices such as printers, web applications, or IoT devices (bring your own devices).
Author