Best Practices for Securing Active Directory
Microsoft created Active Directory (AD), a directory service for Windows Domain Networks. It is part of the Windows Server operating system as a set of processes and services. Active Directory was initially only employed for centralized domain management. However, over time, Active Directory evolved into a “catch-all” term for a variety of directory-based identity-related services. It is the major method used by almost 90% of Global Fortune 1000 firms to offer seamless authentication and authorization.

1. Active Directory Structure
Objects – In Active Directory, an object is a fundamental piece of data. Various types of object information can be stored in Active Directory, including: users, groups, computers, and printers.
Domains – A domain serves as the fundamental unit for assembling connected objects. Domains typically connect to corporate divisions. For instance, a business has distinct departments for accounting, manufacturing, and sales and can have domains with the names accounting, manufacturing, and sales.
Organizational Units – There are frequently too many things in a given domain to manage in a single group. Fortunately, building one or more organizational units, commonly known as OUs, in Active Directory is possible. Objects within a domain can be organized using OUs without the additional work and inefficiencies.
2. Best Practices
Due to the high number of Active Directory capabilities, it is important that rules and metrics are implemented to ensure the security of the entire infrastructure. Administrators can use the practices described in this document to make the network a more resilient and secure environment.
Active Directory encompasses the entire network, including devices and people, so that they can communicate with each other.
Large networks tend to be more complex to manage and there is often a failure to manage the people and equipment present in the network.

2.01. Accounts
Network users have high importance in network security. As these are the most common targets in a cyber attack, it is important that their accounts are properly implemented, regarding access, privileges, network capabilities, and account modification.
- Use security groups instead of explicitly assigning privileges to user accounts.
- Give each user only the minimal rights necessary for them to fulfill their job, strictly adhering to the least privilege paradigm.
- The accounts of employees who leave the company are immediately deactivated.
- Monitor inactive accounts and disable them if they are no longer needed.
- Monitor user account changes for unauthorized modifications to an AD user.
- Password metrics implementation: Expiration and Complexity
- Account Segmentation: It is important that accounts be created for each type of use. The administration accounts should only be used to administer the network.
- Implementation of MFA system for all accounts.
One of the most important aspects is the least privileged approach; where each user has access only to what is strictly necessary to perform his daily duties. A common mistake is normal users with privileges higher than they should have, leading to a possible attack vector for a malicious actor to escalate privileges on the network.
2.02. Domain Administrators
A Domain Administrator is a user with high permissions in Active directory networks. This user can modify the configuration of Active Directory servers and any content stored in the Active Directory network. This includes creating new users, deleting users, altering their ACLs and permissions, managing AD groups, and so on.
Some of the best practices within this context are:
Enable the “Account is sensitive and cannot be delegated”.
- Stop our privileged accounts from giving the attacker access to the delegate-level token.
Enable the “Smart card is required for interactive logon”.
- For the organization to comply with this criteria, a solid public key infrastructure (PKI) must be in place, and all users must have access to smart cards and smart card readers.
Enable “Deny access to this computer from the network”.
- This security setting determines which users are prevented from accessing a device over the network.
Enable “Deny log on as a batch job”.
- Prevents administrators or operators from scheduling tasks using their personal accounts.
Enable “Deny log on as a service”.
- Identifies which users are unable to access the service applications using the device.
Enable “Deny log on through RDP”.
- Defines the accounts that are prevented from logging on using Remote Desktop.
2.03. Local Administrator
A local administrator account is a user account that can manage a local computer.
The local administrator account is an account that is often targeted within a corporate network, and this account should be deactivated if possible.
One of the main reasons to disable this built-in Administrator account is that it cannot be locked out, even after several failed logins, which makes this account an interesting target for a malicious actor to perform brute force attacks that attempt to guess passwords.
In addition to the situation explained above, this account has a known security identifier (SID) and there are several tools that allow authentication to be performed by using the SID instead of the account name, meaning that even if the administrator account is renamed, a malicious actor can launch a brute force attack using the SID to log in.
Another common mistake with these kinds of accounts is to set the same password for several computers. Once the password is discovered, malicious actors are capable of performing a spray attack on several machines.
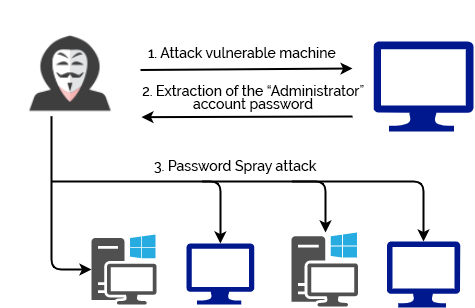
Figure 1: Password spray attack illustration.
2.04. File Shares and Printers
File Shares
- File Shares allow domain users to share files in their folders. It is important that users are assigned to restricted groups, and that the permissions on each share are according to the group’s needs. For example, it will not make sense for a normal user to have write permissions on the financial department share.
- Activate SMB Signing
- If SMB signing is not active, there is a risk that SMB traffic will be intercepted. This means that an attacker present on the network can probably steal the active sharing sessions on your network.
Printers
- Although printers often go unnoticed, something extremely found during network audits are printers that use passwords by default or without any kind of authentication. Importantly, many printers contain access to their own shares and shares where files with sensitive content are often found. Printers on the network should have their default password changed to prevent access by malicious actors.
2.05. LLMNR
LLMNR (Link-Local Multicast Name Resolution), is a protocol that comes enabled by default on Windows systems, working for name resolution over IPv4 and IPv6.
This protocol is commonly used in organizational networks but presents several risks, such as exploiting the Server Message Block (SMB).
When a user tries to access a share, and the IP does not exist or is not recognized, an attacker on the network declares itself as being that IP, and the system tries to connect with the keys to the attacker, thus providing the user and the hash.
Attack example:
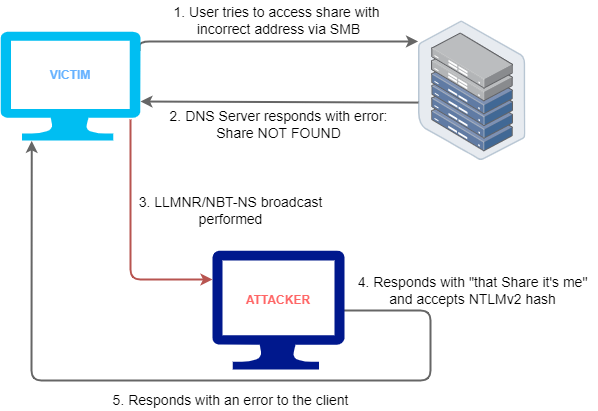
Figure 2: LLMRN relay attack workflow.
Many people in the cybersecurity community consider this a legacy protocol, and because of its lack of security and easy exploitation, it should be disabled.
This protocol can be disabled using, for example, the Group Policy Editor.
2.06. Group Policies
Group Policies (GPO) are an easy way to apply multiple settings to machines and users divided into groups. There are numerous policies that must be implemented on users’ computers in order to keep the entire ecosystem protected, thus acting as an aid to the Active Directory settings themselves.
Security Technical Implementation Guides
Security Technical Implementation Guide (STIG) is a set of configuration standards composed of the cybersecurity specifications for a given product.
In order to improve overall security, a methodology for safeguarding protocols within networks, servers, computers, and logical architectures is made possible through the use of STIGs.
When these guidelines are followed, vulnerabilities are further decreased by improving security for software, hardware, and physical and logical structures.
More details about this topic can be found below.
Security Technical Implementation Guides (STIGs) by DoD
2.07. Powershell / CMD Limitation
Depending on the role of each worker, most of the time there is no need for the employee to use CMD or Powershell, and these can be a great tool for a malicious actor to obtain device and network information and execute files.
Limiting access to CMD and Powershell should be performed on machines where employees have no need to use them, so before implementing this measure, a survey should be done on the need to use these tools for each user.
This limitation can be done by using GPOs for the group that does not need to use the tools.
2.08. Monitor AD Events
AD monitoring is the process of observing the AD environment through various techniques used to reduce and resolve issues affecting the entire service directory in a Windows network.
Normally, AD is monitored by Microsoft’s built-in System Center Operations Manager (SCOM).
Looking for signs of compromise:
- Changes in privileged groups
- Fast tries using wrong password attempts
- Use of local administrator accounts
- A fast number of locked-out accounts
- Disabled or removal of antivirus rules/software
- Account lockouts
- Check all actions performed by privileged accounts
Relative Resources
Microsoft, which owns the product, contains detailed steps and other security practices on its official website that can be followed and applied in ecosystems:
Best Practices for Securing Active Directory
Conclusion
Considering the large scale on which Active Directory is used and the diverse amount of industries in which it is present, it is important to keep in mind that its security should be a basic principle of an organization with this system in use.
This topic should be addressed internally and result in periodic audits to identify and mitigate possible risks or reinforce the security chapter. It is also important to notice that the points identified in this article are just a few security measures that should be aligned with the required security. However, there are more actions that can be implemented to make Active Directory networks a safer and more resilient place against cyber threats.
Author
Bernardo Rodrigues